
Cloud adoption has become mainstream. Cloud computing is rapidly mushrooming Enterprise IT. But the increased intent towards the cloud has also intensified security concerns.
IBM Institute for Business Value (IBV) and IBM X-Force Incident Response and Intelligence Services (IRIS) recently released a cloud security report indicating – 66% of users rely on cloud providers for baseline security. Thus, security has become a top priority for SaaS vendors.
In this article, we will discuss common security threats. Also, we’ll cover the types of cloud security mechanisms that ensures information security.
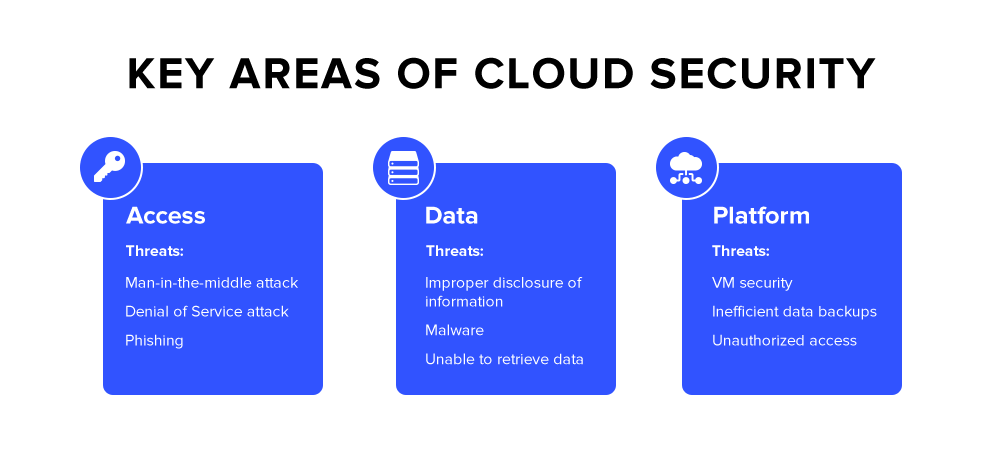
Key areas of cloud security
There are three main areas of security concerns in the cloud-based applications – access, data, and platform. Let us examine these in detail.
1. Access security
Cloud offers a centralized data storage mechanism. “Who can access data” is strictly governed by access rights and privileges. SaaS providers add another level of security to stop wrong (unauthorized) people from accessing the resources and information stored in the cloud.
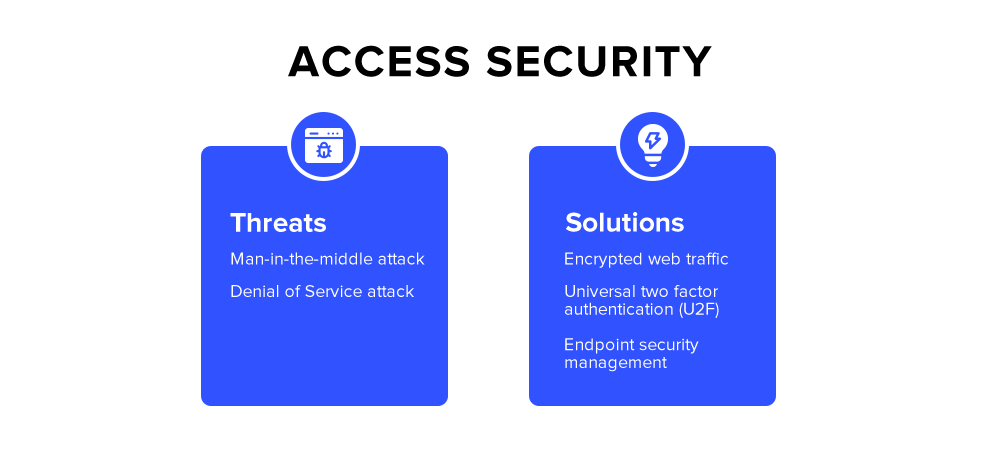
There are three common cyber-attacks which target access privileges:
- Man in the Middle attack: here, an attacker gains access to resources by intercepting web traffic.
- Denial of Service (DoS) attack: here, the perpetrator makes the resources unavailable to the intended users by disrupting the services of the host.
- Phishing attack: here, the attacker steals the credentials of users/employees and uses the information for malicious activities.
Cloud service providers and SaaS companies take care of access security by using the following techniques:
Encrypted web traffic
The transport layer security (TLS) is a security protocol for web traffic. The secure socket layer (SSL) encrypts communication between a client and a server to send messages. It uses an information passing mechanism known as SSL passthrough. It passes data through a load balancer to a server without decrypting it.
This process ensures identity authorization. An intruder or an unauthorized person cannot decipher the message sent over the internet. It thus eliminates the chances of Man in the Middle attack and Denial of Service attack at the network level.
As a user, you should check for HTTPS notation in the URL. HTTPS indicates that the web page you’re going to visit follows the SSL encryption method.
Universal two-factor authentication (U2F)
U2F or universal two-factor authentication is a method to ensure that only authorized user is accessing the resources. It uses login credentials as well as OTP (one-time-password) to authenticate the user. Users can select receiving the OTP via SMS, email, or phone call.
It is a security mechanism against phishing, session hijacking, man-in-the-middle attack, and malware attacks.
Endpoint security management
Since cloud services give the liberty to use any mobile device to access resources, SaaS providers need to ensure endpoint security. There can be several endpoint devices such as mobile phones, laptops, tablets, point of sale terminals, and even bar code readers.
Endpoint security management involves managing and controlling devices that request access to the corporate network. Depending on the type of device, the cloud service provider can either grant or limit specified access to the user on that device.
All the above measures are crucial to ensure access security on mobile devices.
2. Data security
Modern applications require infrastructure that traditional data centers cannot meet. Gartner forecasts that the Cloud Infrastructure as a Service (IaaS) will grow 24% year over year to meet the demands of modern-day applications and workloads. The increasing trend of storing data on the cloud, has also increased the responsibility of data security on cloud service providers. The following are the data security threats.
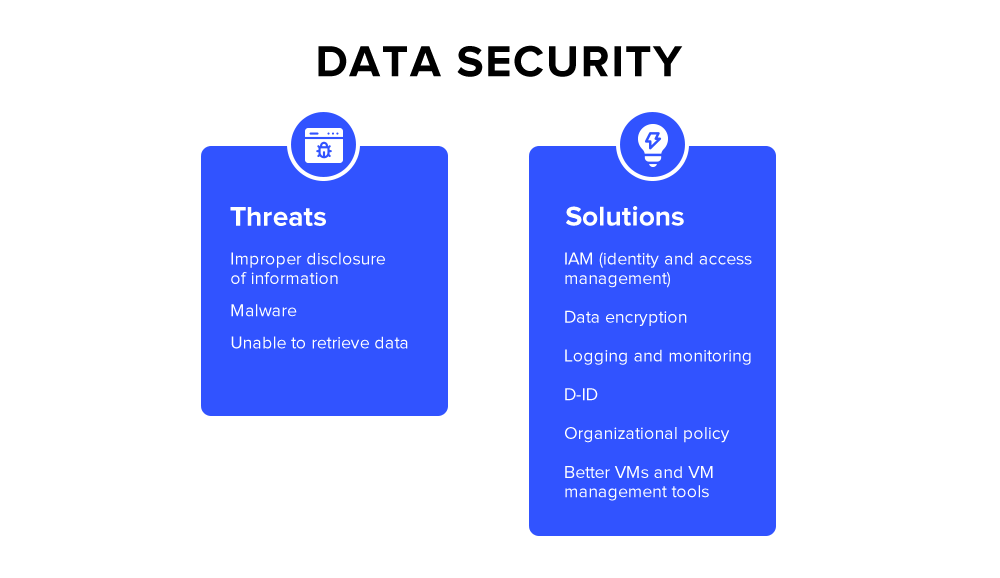
The points of failure in data security involve the ease of accessing data, receiving corrupt data or storing illegal data, unsanitized data that can compromise the application or internal systems, and data transfer. Another crucial security measure that cloud service providers should ensure is PII (Personally Identifiable Information). PII is any data that can identify an individual. The following are the common data storage traps-
- Improper disclosure of your data by your employees (such as accidentally sending credit card details or social security numbers).
- Your application giving out harmful data (such as sending phishing information through malware).
- Storing data in an insecure place without proper security protocols.
Data security solutions
The following are the solutions that SaaS companies deploy for data security:
- IAM (identity and access management): It is a framework of policies that ensures that only authorized people have appropriate access to technology and resources.
- Data encryption: It is the process of encoding the information to prohibit attackers from making sense of sensitive information.
- Logging and monitoring: It is the process of collection and analysis of request logs. It also helps in monitoring the availability of infrastructure services.
- D-ID: It involves biometric protection to eliminate the risk of identity theft. Office premises and personal devices of authorized people are D-ID secured.
- Organizational policy: Cloud vendors plan and implement strict policies to identify, report, and act on vulnerabilities.
- Better VMs and VM management tools: Finally, companies invest in VM and VM tools (Virtual Machine tools) to administer the operations and process of the cloud environment. VM tools help in cloud security in a lot of ways. It provides alerts, monitors processor and memory allocation to virtual machines. It also takes care of dynamic resource allocation and future requirements prediction.
[Also read: What is a cloud-based CRM and how does it benefit your business?]
3. Platform Security
A platform is a physical system that houses and delivers information. Also known as Platform as a Service, a cloud platform provides an on-demand environment for developing, testing, delivering, and managing software applications. Vendors / SaaS Platforms should ensure the security of physical and virtual hardware.
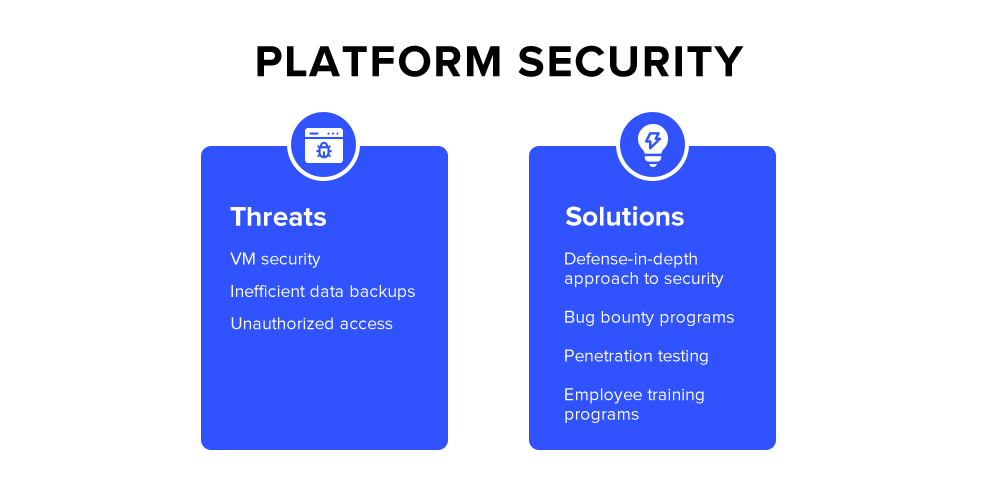
Platform security addresses the following concerns:
- How does the cloud provider secure its platform?
- Is data in the cloud secure?
- Are VMs appropriately isolated?
- Are physical devices properly secured and checked?
- Who has access to my data?
In order to address the above concerns, most of the cloud service providers follow a defense-in-depth approach to security. Defense-in-depth is an information assurance strategy. It provides multiple defensive measures for the instances of security control failure or exploitation of a vulnerability.
Organizations also manage controls over access rights and privileges to ensure platform security. SaaS organizations frequently launch bug bounty and penetration testing programs and invest in training programs so that its employees never compromise cloud security.To further enhance security, especially in early-stage companies, regular pentests for small businesses are adopted as a proactive measure to identify and mitigate vulnerabilities.
Concluding remarks
As the new decade begins, cloud adoption is going to increase. Scalability, flexibility, and security are the major growth drivers for SaaS products across the globe. Oracle and KPMG cloud threat report 2020 reveals that 75% of the business representatives feel that the cloud is more secure than their data center.
While investing in a cloud-based platform, you can question the vendor about access, data, and platform securities. An easy way to know this is to check for ISO 27001 certification. You can also check for GDPR (General Data Protection Regulation) compliance.
LeadSquared is an ISO 27001 certified, GDPR compliant, SaaS CRM platform. It has instituted organization-wide processes to ensure cloud security for all its customers. Details. Also, check out LeadSquared cloud-based CRM software built for high velocity sales.
Cloud Security FAQs
Cloud security or cloud computing security refers to a set of policies, controls, procedures, and tools that work together to protect data, access, and platform.
Businesses have legal obligations to keep their customer data secure. While storing data in the cloud, security measures are crucial to ensure that the information is safe and accessible only to authorized users.
Traditional data storage involved perimeter-based security models. Cloud provides ease of access to data but, at the same time, it makes it easier for traffic to bypass perimeter defenses. Therefore, cloud security models incorporate additional layers of security protocols to ensure confidentiality, availability, and integrity of information.








