-
1. What is HIPAA Compliance?
-
2. HIPAA – Beginnings
-
3. Protected Health Information (PHI)
-
4. The 5 Key Rules of HIPAA Compliance
-
5. Who Needs to Be HIPAA-Compliant?
-
6. The Role of Technology in HIPAA Compliance
-
7. Popular Tech Tools for Handling Healthcare Data
-
8. How CRMs Help Healthcare Providers Remain HIPAA Compliant
-
9. Steps to Achieve HIPAA Compliance
-
10. Consequences of HIPAA Violations
-
11. Healthcare Marketing and HIPAA Regulations
-
12. HIPAA Compliant Communication via Email or Text
-
13. HIPAA Compliance Checklist
-
14. Looking for a HIPAA-Compliant Healthcare Platform?
-
15. FAQs
This Guide Is For
This HIPAA compliance guide is for anyone involved in the healthcare space. Whether you’re a healthcare practice worried about handling patient data, a marketing professional who wants to ensure your campaigns are compliant, or part of the admin team checking everything runs smoothly, this guide breaks down the essentials.
Turning the idea of HIPAA compliance less daunting and more actionable – that is the aim of this guide.
What is HIPAA Compliance?
What happens to a patient’s health information once they share it with their doctor or, say, their pharmacist?
For the most part, they may not care — they assume it’s safe, private, and out of reach for prying eyes. But behind the scenes, there’s a framework that makes this trust possible.
A set of rules that ensures accountability when sensitive healthcare data is mishandled. With consequences that hit hard, these rules leave no room for carelessness — or for those with bad intentions to slip through unnoticed.
These rules that stand guard over important patient information are termed HIPAA.
For healthcare organizations, HIPAA is not just a set of agreements one can skim through like a terms-and-conditions pop-up before clicking “I agree.” Without consistent actions, the pact can easily be broken, which leads way to dire consequences.
Because, to keep sensitive patient data from slipping through the cracks, to ensure only the right people have access to it, and to protect it against breaches that could ruin reputations overnight… it takes effort.
So, whether you’re a small clinic, a global healthcare provider, or even a tech vendor in the healthcare domain, understanding HIPAA isn’t optional — it’s essential.
In this guide, we’ll cut through the legalese and get to the heart of HIPAA: who it applies to and how it impacts the way healthcare operates in today’s digital-first world.
But to really appreciate why HIPAA matters, we need to first rewind the clock to a time when healthcare was beginning to evolve — a time when privacy wasn’t always a given.
HIPAA – Beginnings
Back in 1996, the healthcare world was at a crossroads. The digital revolution was beginning to reshape industries, and healthcare was no exception. Patient records, once locked away in file cabinets, were starting to move online. It was efficient, yes — but it also raised questions no one had to ask before: How do we keep this sensitive information safe? Who gets to see it, and who doesn’t?
That’s where HIPAA—the Health Insurance Portability and Accountability Act—came into being.
Signed into law by President Bill Clinton, the original purpose of HIPAA wasn’t just to protect privacy — but to make healthcare more efficient, fair, and accessible. It tackled challenges like ensuring continuity of coverage for employees switching jobs, protecting individuals with pre-existing conditions, and addressing “job lock” — a situation where people felt trapped in their jobs for fear of losing health insurance. It also sought to simplify the industry’s growing reliance on electronic transactions.
However, as electronic health records became the norm, the potential risks became clearer. Medical data flowing through networks and across borders meant protecting patient privacy was a matter of urgency.
So, HIPAA added a new layer of safeguards: national standards to shield Protected Health Information (PHI) from misuse or unauthorized access.
Over the years, these regulations have evolved — and continue to do so — to address new challenges in an ever-changing digital landscape.
But what exactly constitutes the information that these rules strive to protect?
This brings us to a term we just touched on: Protected Health Information, or PHI — which is the key element of everything HIPAA is built to safeguard.
Protected Health Information (PHI)

Healthcare is often a deeply personal matter. For many, sharing their health conditions with even close family or friends can feel uncomfortable. There’s something about laying bare our vulnerabilities that makes us hesitate. Given that, how many of us would want someone outside our close personal circle to know about our diagnosis, treatment plans, or long-term conditions?
This rightful sense of hesitation, of wanting to keep something so personal under wraps, is what makes Protected Health Information (PHI) so relevant.
At its core, PHI covers any piece of information that links you to your health status. If someone could use some detail to identify you and learn about your medical history, treatments, or billing, it falls under the protection of HIPAA.
This could be:
- Personal identifiers: The simple stuff, like your name, address, phone number, and so on.
- Medical records: Your diagnosis, treatment data, prescriptions—anything that paints the picture of your health journey.
- Billing information: From your insurance details to payment records.
- Health records: Lab results, imaging reports, and other medical notes that track your well-being.
- Other identifiers: Social security numbers, medical record numbers, and even biometric data — all crucial pieces that tie back to you.
Whether it’s shared through an email, on paper, or spoken aloud, PHI is protected by rules that ensure it’s only accessed by the right people, for the right reasons.
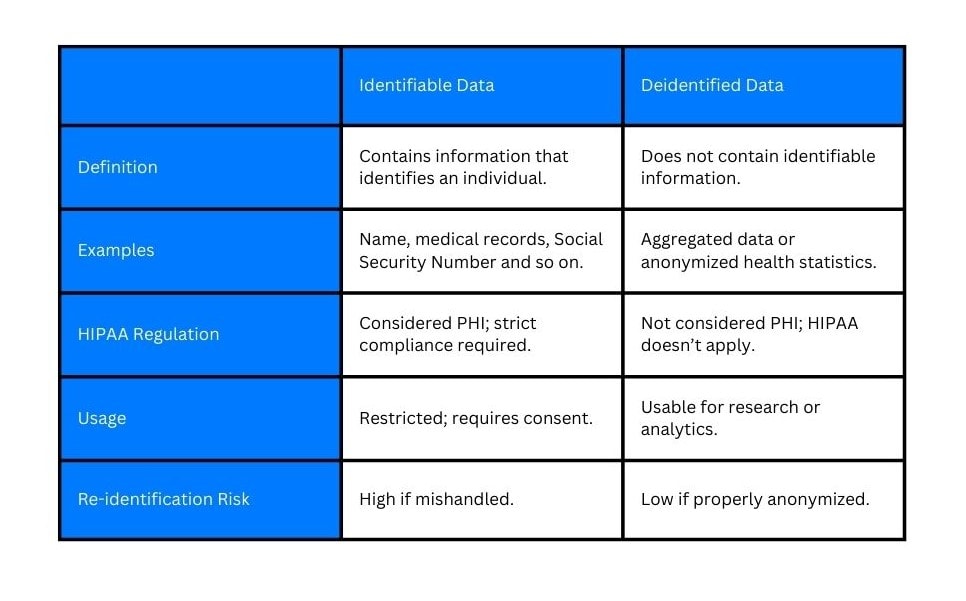
Identifiable data
Not all information is created equal. Some are prioritized for protection over others.
Firstly, we have unique identifiers — your name, your diagnosis, your contact details — these are the pieces that make up what we call “identifiable data.” This is the kind of information that could easily be traced back to you, which is why it’s protected under HIPAA.
But not all health data needs to stay tied to a person. Sometimes the information can be stripped of the personal markers that link to an individual. This is called de-identified data.
Though still relevant, these data no longer fall under the same tight protections of HIPAA.
If you are having trouble imagining how de-identified data would look like, here are some examples:
- Age, but without the specific birthdate (e.g., 40-50 years old, rather than “January 1, 1985”).
- Geographic information, such as a patient’s state or zip code, but not the full street address.
- Diagnosis details stripped of specific dates and identifiers, leaving only the general medical condition (e.g., “high blood pressure” without the patient’s exact medical history).
- Treatment types or procedures performed
,without any connection to a specific individual.
De-identification of PHI allows healthcare providers to share valuable data for research or analysis while still respecting individuals’ privacy. Removing identifiers ensures that even if data is exposed, it can’t be tied back to an individual.
We’ve seen what Protected Health Information is and why it matters. Now, let’s look at the pillar rules of HIPAA that exist to protect it.
The 5 Key Rules of HIPAA Compliance
You may have figured out already that HIPAA isn’t just one sweeping law. It’s a collection of carefully constructed rules designed to address specific challenges in healthcare data privacy and security.
Let’s see what they are.
1. The Privacy Rule
The Privacy Rule sets the boundaries. It ensures that Protected Health Information (PHI) doesn’t end up in the wrong hands. Individually identifiable health information, which includes verbal, electronic, or paper data that can be associated with a specific individual, becomes PHI under the Privacy Rule.
Not just restrictions—it also grants patients rein to their own data, allowing them to access their records, request corrections, and understand exactly how their information is being used. It also limits disclosures to only the minimum necessary information, ensuring that healthcare data is not unnecessarily exposed.
2. The Security Rule
If the Privacy Rule is about control, the Security Rule is about protection. This rule is specifically concerned with safeguarding electronic Protected Health Information (ePHI).
For this, it makes healthcare organizations implement robust measures across three key areas:
- Administrative safeguards: Policies, procedures, and workforce training to ensure ePHI is handled securely.
- Physical safeguards: Controls to protect physical access to servers, workstations, and other hardware, such as locked server rooms or badge-restricted access.
- Technical safeguards: Tools like encryption, secure login protocols, and access controls to ensure only authorized personnel can access sensitive data.
All in all, the Security Rule ensures ePHI remains safe from unauthorized access, breaches, or theft, both online and offline.
3. The Breach Notification Rule
Mistakes happen, and when they do, the Breach Notification Rule ensures transparency. In the event of a data breach, HIPAA-covered entities must notify affected individuals, the Department of Health and Human Services (HHS), and, in some cases, the media. This rule acts as an accountability checkpoint, holding organizations responsible for keeping patients informed when their data may have been compromised.
4. The Enforcement Rule
Rules without consequences are just suggestions — and HIPAA doesn’t deal with suggestions. The Enforcement Rule is where accountability becomes non-negotiable.
This rule spells out exactly what happens when organizations fail to comply with HIPAA. Penalties can range from hefty fines to public exposure and, in extreme cases, even criminal charges.
This rule also allows the United States Department of Health and Human Services (HHS) to investigate complaints, conduct audits, and ensure that organizations uphold HIPAA compliance.
5. The Omnibus Rule
The Omnibus Rule is the catch-all. This rule strengthens existing protections, particularly for business associates who handle patient data. It makes it clear that contractors, vendors, and third-party providers are just as responsible for safeguarding sensitive health information as covered entities.
Together, these rules leave no room for ambiguity. But the question remains: who all falls under HIPAA’s watchful eye?
Who Needs to Be HIPAA-Compliant?

When we talk about HIPAA compliance, most people think of the obvious players: hospitals, clinics, and insurance providers – the ones directly interacting with patients. But the web of responsibility is much wider.
At the forefront are the covered entities—healthcare providers, insurers, pharmacies—organizations that deal with protected health information as part of their core operations. Their role is clear, and so is their accountability.
Then there are the business associates—the less visible yet equally critical players. They include the tech platforms managing patient records, insurance companies processing claims, billing services handling payment information, and more. Business associates work on behalf of covered entities like hospitals or clinics, often using PHI.
In short, if you handle patient data in the healthcare industry, directly or indirectly, you’re part of the chain of trust.
The Role of Technology in HIPAA Compliance
Handling sensitive patient data manually or relying on outdated methods isn’t just inefficient — it’s risky. Paper-based records can be misplaced, human errors in data entry can lead to breaches, and monitoring who accessed what information can become a logistical nightmare.
Technology becomes indispensable here:
Consistency and accuracy
Tech minimizes the errors that are common in manual processes. Automated systems ensure data is entered and stored consistently and accurately.
Scalability
As healthcare organizations grow, managing more data becomes complex. Technology scales with the organization, ensuring compliance measures remain robust.
Monitoring and auditing
Technology allows for real-time monitoring, audit trails, and automated reports that make compliance tracking straightforward and transparent.
Speed and security
Digital tools encrypt sensitive data, secure it during transmission, and allow only authorized access — things that are hard to achieve with physical files or outdated software.
Proactive risk management
Advanced systems detect potential vulnerabilities or breaches before they become critical issues, something that isn’t possible with manual oversight.
Popular Tech Tools for Handling Healthcare Data
Here’s a list of popular tools used in healthcare that involve data handling.
Electronic Health Records (EHR) systems
- EHRs are centralized platforms for storing, accessing, and sharing patient data. They are foundational for managing protected health information (PHI).
- Examples: Epic, Cerner, Veradigm.
Identity and Access Management (IAM)
- Tools like multi-factor authentication and access control systems that ensure only authorized personnel handle PHI.
- Examples: Okta, Microsoft Azure AD.
Cloud storage
- Secure cloud storage services allow data to be accessed securely from anywhere while adhering to HIPAA regulations.
- Examples: AWS for Healthcare, Google Cloud Healthcare API.
Healthcare CRMs
- CRMs in healthcare help manage patient relationships by integrating data from multiple sources like EHRs, billing systems, and communication platforms. They also streamline workflows, improve patient communication, and aid in compliance by securing patient information.
- Examples: LeadSquared’s HIPAA-compliant Healthcare CRM, Salesforce Health Cloud, HubSpot for Healthcare.
Secure communication platforms
- Messaging and telehealth platforms that ensure sensitive communications are encrypted and secure.
- Examples: LeadSquared’s Patient Communication Module, TigerConnect, Zoom for Healthcare.
How CRMs Help Healthcare Providers Remain HIPAA Compliant
Healthcare has always been about more than just treatments. It’s also about relationships — with patients, providers, and everyone in between. But as the industry becomes increasingly complex, maintaining those relationships and keeping track of sensitive data becomes a challenge. That’s where Healthcare CRMs come in.
While they’re not as foundational as EHR systems, CRMs have carved out a vital role in the healthcare tech ecosystem by focusing on the patient management, relationship, and communications sides of care, all while ensuring HIPAA compliance.
These systems do more than store phone numbers or appointments. They provide a dynamic way to connect with patients, streamline administrative processes, integrate with other tools used in healthcare, and most importantly, ensure that all the data stays safe and HIPAA compliant.
Here’s what CRMs can do to ensure HIPAA compliance and how providers can best use the tool within the bounds of HIPAA.
Bolster data security and privacy

Encryption: This ensures that data is converted into unreadable code while in transit or at rest, keeping it safe from unauthorized access. It also ensures that only those with the right decryption keys, passwords, or access can view the data.
Role-based access: Not every team member needs access to every bit of data. Role-based access controls allow healthcare organizations to set specific permissions for staff, ensuring that employees only have access to the information they need to perform their job duties. This limits the risk of unauthorized data exposure.
Backups: Data loss can have disastrous consequences. Automated backups are essential in case of a system failure, ensuring that sensitive patient health information remains intact and recoverable. Whether it’s a cloud-based solution or on-premises storage, regular backups make sure that patient data isn’t lost due to human error or technical failure.
This is only the pure data protection side of a healthcare CRM. A big part of HIPAA compliance also lies in ensuring that healthcare communication is secure. HIPAA-covered entities often handle sensitive data across multiple channels, from emails to patient portals. A CRM makes it easier to safeguard these interactions.
HIPAA compliant communication
Secure email: Your average email is not HIPAA-compliant, but many healthcare CRMs offer encrypted email functionality — this ensures any communication containing Protected Health Information (PHI) is protected in transit, preventing unauthorized access.
Patient portals: These portals act as a secure bridge between providers and their patients. Patients can access their medical records, schedule appointments, or send messages through the portal.
Telehealth: With the rise of virtual care, CRMs designed for healthcare now integrate telehealth features. They use encrypted video conferencing and secure messaging platforms so that healthcare practices can consult with patients remotely while maintaining HIPAA compliance.
Integration with EHR/EMR
A CRM doesn’t exist in isolation, and for HIPAA compliance to be effective, it must play nicely with your other systems—like Electronic Health Records (EHR) or Electronic Medical Records (EMR).
Benefits of integration with EHR/EMR:
Interoperability: A well-integrated CRM allows patient data to flow smoothly from EHRs, reducing the need for manual entry and minimizing errors. This ensures easy access to comprehensive patient information, enhancing care coordination and workflow efficiency.
Centralized data management: When a CRM is integrated with EHR/EMR systems, healthcare organizations can centralize patient data, making it easier to manage records while maintaining compliance. It also helps keep data consistent and accurate, which is crucial for audits and patient care continuity.
Compliance tracking: Integration allows healthcare organizations to track how patient data is used across systems, ensuring that all data access is HIPAA-compliant. This can include keeping audit trails of who accessed data and when which is crucial for compliance reviews and investigations.
Integrating CRM with EHR/EMR systems also means there’s no disconnect between patient interactions and clinical data, making it easier to uphold HIPAA standards.
HIPAA compliance often translates to more restrictions for a healthcare provider. But a healthcare CRM excels in ensuring providers seldom feel boxed in—offering the best of what’s possible while staying compliant.
Here’s how a CRM can benefit healthcare providers without compromising HIPAA compliance:
- Easy data access
They pull patient data from various sources — EHRs, billing systems, and appointment schedulers — into one place for easier access. - Streamlined patient communication
By automating reminders, follow-ups, and health information distribution, CRMs enhance patient communication while maintaining security and compliance. - Improve workflow efficiency
CRMs can automate repetitive healthcare operations to reduce administrative burdens and free up healthcare professionals to focus on patient care. - Ensure compliance
Many healthcare CRMs are designed with HIPAA compliance in mind, offering encryption of healthcare data, role-based access controls, and much more. - Data-driven insights
CRMs offer detailed insights into patient data, helping healthcare organizations track trends, measure performance, and make informed decisions to improve patient outcomes. - HIPAA-Compliant Patient Portals
Patient portals integrated into CRMs offer secure, 24/7 access to personal health information, lab results, and appointment schedules, all while ensuring compliance with HIPAA’s privacy and security standards.
Steps to Achieve HIPAA Compliance
Data security breaches are all too common when the right measures aren’t taken to protect sensitive patient data. To put it into context, here are some statistics on healthcare data breaches that happened in the United States:
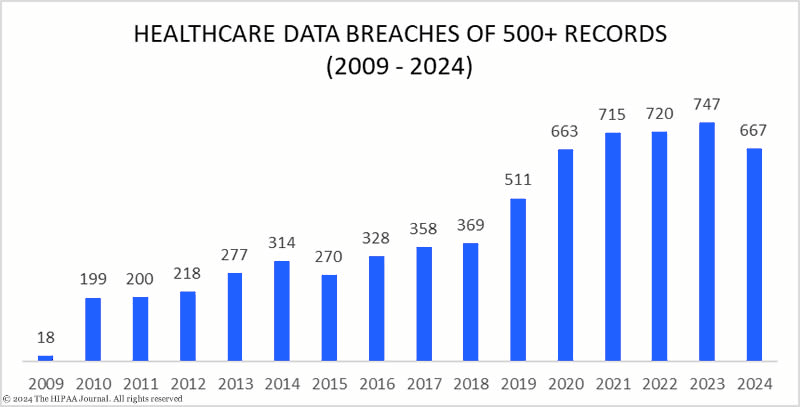
Given this, what are the steps we can take to prevent such unfortunate mistakes?
1. Conducting a risk assessment
When it comes to protecting sensitive health information, the first step isn’t to build walls — it’s to find the cracks. A risk assessment serves as a spotlight, illuminating where vulnerabilities lurk and how breaches could happen.
What does this involve?
- Trace the journey of PHI: Map out every place patient data lives, travels, and rests — from digital records to physical charts.
- Uncover weak links: Examine where things could go wrong, whether it’s a poorly secured workstation, outdated software, or a careless habit.
- Document the findings: Turn observations into a prioritized to-do list. Which risks pose the greatest threat? Which need immediate action?
By peeling back the layers, you can address compliance gaps before they turn into costly mistakes.
2. Implementing safeguards
Physical safeguards: This is the groundwork. Think locked doors, secured filing cabinets, and limited access to areas housing servers or patient records. These measures ensure only those who need to can physically touch PHI.
Administrative safeguards: Policies and people are just as critical as locks and passwords. These safeguards define who can access what and under what circumstances. Role-based permissions and regular workforce training help ensure everyone knows the rules and why they matter.
Technical safeguards: For electronic PHI (ePHI), technology acts as both the shield and the gatekeeper. Encryption makes data unreadable to unauthorized eyes, while access controls and secure networks fortify the system against breaches.
3. Regular employee training
Compliance doesn’t just live in policy manuals — it’s reflected in the actions of every employee, every day. HIPAA regulations are only as strong as the people who implement them, making regular training a crucial element of HIPAA compliance.
4. Auditing and monitoring for compliance
Regular auditing and vigilant monitoring ensure that HIPAA standards are upheld, even as new risks emerge.
Internal audits: Conduct periodic reviews of systems, workflows, and practices. The goal? To uncover weak spots before they become vulnerabilities and to refine safeguards as needed.
Technology that monitors: Automated monitoring tools do more to save time. These tools track access logs, flag unusual activity, and alert you to potential breaches before they escalate.
Consequences of HIPAA Violations
What happens when you violate HIPAA regulations? From fines to legal ramifications, it’s an invitation for all sorts of trouble.
1. Financial penalties
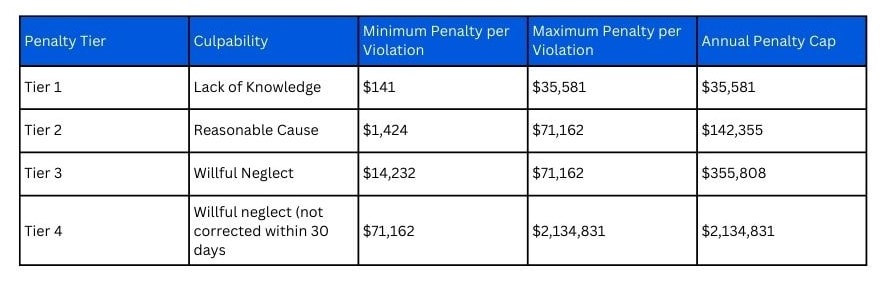
Financial consequences of HIPAA violations can be severe and are designed to deter any lapses in handling PHI. But the costs aren’t just a one-size-fits-all penalty — they’re tiered based on the severity of the violation.
The below image showcases the penalties levied for HIPAA violations
2. Legal ramifications
HIPAA violations can also result in serious legal consequences. Affected patients may file civil lawsuits for negligence or data misuse. Criminal penalties can include imprisonment for up to 10 years, especially for intentional misuse of PHI. Additionally, some states impose their own penalties, adding to the legal burden for violators.
3. Reputational damage
The next thing to be wary of is reputational damage. With it, patient trust in data security erodes. Negative media coverage amplifies the damage, often leading to public backlash. Over time, this reputational harm can hinder partnerships with other organizations and lead to a loss in patient retention, ultimately affecting the bottom line.
Healthcare Marketing and HIPAA Regulations
When it comes to marketing in healthcare, there’s a fine line between reaching your audience and respecting their privacy. HIPAA ensures that patient information stays confidential, but it doesn’t mean healthcare organizations can’t advertise their services.
HIPAA regulations emphasize patient consent, making it clear that organizations must obtain explicit permission before using identifiable health data for marketing purposes. Even with de-identified data, organizations must be cautious to avoid inadvertently revealing information that could trace back to an individual.
Creating compliant campaigns
1. Leave PHI out of the spotlight
Creating compliant campaigns means removing Protected Health Information (PHI) from the mix. Instead of personal patient data, focus on general health topics, wellness advice, or treatment overviews. Think broad and non-specific—if you keep your messaging general, you’re not only avoiding privacy violations but also expanding your campaign’s reach to a larger audience.
Curious about how these strategies translate to email marketing? This article on HIPAA compilant email marketing covers it in detail. And when you’re ready to put them into action, these 25 healthcare email templates can help you get started.
But before that, here’s a simple table differentiating what can and cannot be included in HIPAA-compliant communication:
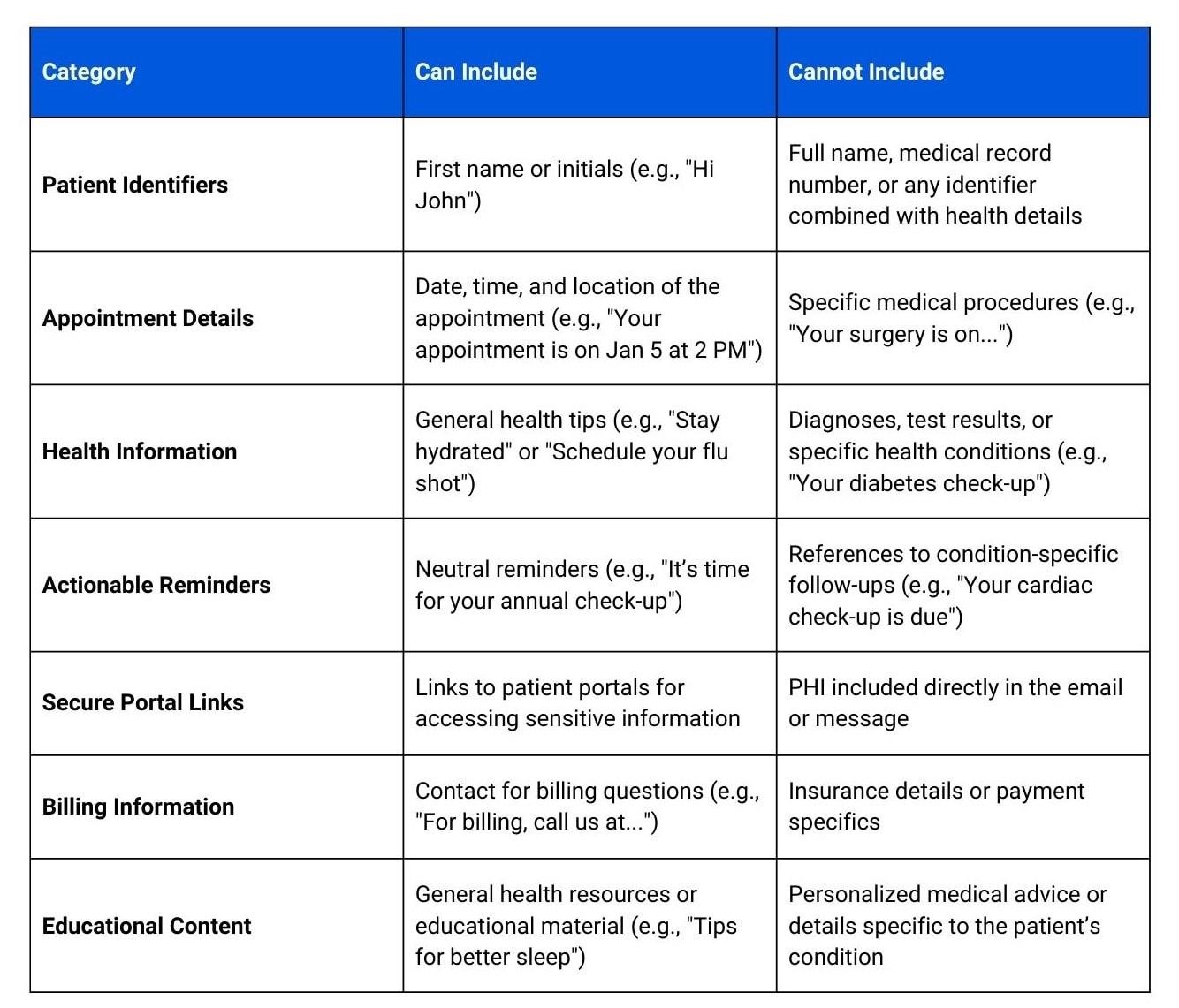
2. Get clear consent
Transparency is key when it comes to using patient data for marketing. HIPAA mandates that patients must give explicit consent before their data is used in any marketing materials. This can be done through consent forms, clear opt-in options, and transparency around how their information might be used — from direct mail to email campaigns. By respecting their autonomy, you’re not just staying compliant, but you’re building trust with your patients.
HIPAA Compliant Communication via Email or Text
HIPAA-compliant messaging requires more than just good intentions. Here’s what to check before sending any sensitive data.
Encryption is essential
To ensure HIPAA compliance, email and text messages containing PHI must be sent through encrypted platforms. Secure email systems or patient portals offer end-to-end encryption to protect sensitive data from unauthorized access.
Avoid unsecured platforms
Never use unencrypted email services or SMS for PHI. Mainstream email platforms and regular texting aren’t secure and leave patient information vulnerable to interception.
Use HIPAA-Compliant messaging systems
Secure, HIPAA-compliant messaging systems are necessary for safe communication. Look for platforms with encryption, two-factor authentication, and audit logs to maintain compliance.
HIPAA Compliance Checklist
Use this checklist to assess your organization’s HIPAA compliance and ensure you’re taking the right steps to protect patient data.
1. Assess privacy and security policies
- Review existing privacy and security policies for alignment with HIPAA regulations.
- Ensure policies are comprehensive, covering physical, administrative, and technical safeguards.
2. Conduct regular risk assessments
- Perform periodic risk assessments to identify vulnerabilities and gaps in compliance.
- Address findings promptly to minimize risks.
3. Implement safeguards
- Ensure that physical, technical, and administrative safeguards are in place to protect PHI.
- Encrypt data, control access and ensure appropriate storage of sensitive information.
4. Provide employee training
- Train staff on HIPAA regulations, breach detection, and PHI handling.
- Offer refresher courses regularly to maintain compliance awareness.
5. Use secure communication methods
- Use HIPAA-compliant communication tools for emails, texts, and patient interactions.
- Ensure encryption and patient consent before sending PHI electronically.
6. Maintain documentation and auditing procedures
- Keep records of all compliance efforts, including training, audits, and risk assessments.
- Regularly audit your system for potential non-compliance or gaps.
7. Review Business Associate Agreements
- Ensure that all third-party vendors handling PHI are HIPAA-compliant.
- Update Business Associate Agreements (BAAs) to reflect current regulations.
8. Prepare for breach notification
- Establish a protocol for reporting breaches, including notification to affected patients, HHS, and media if necessary.
- Ensure that breach response measures are regularly tested.
If you wish to know more, here’s a more comprehensive checklist for HIPAA compliance.
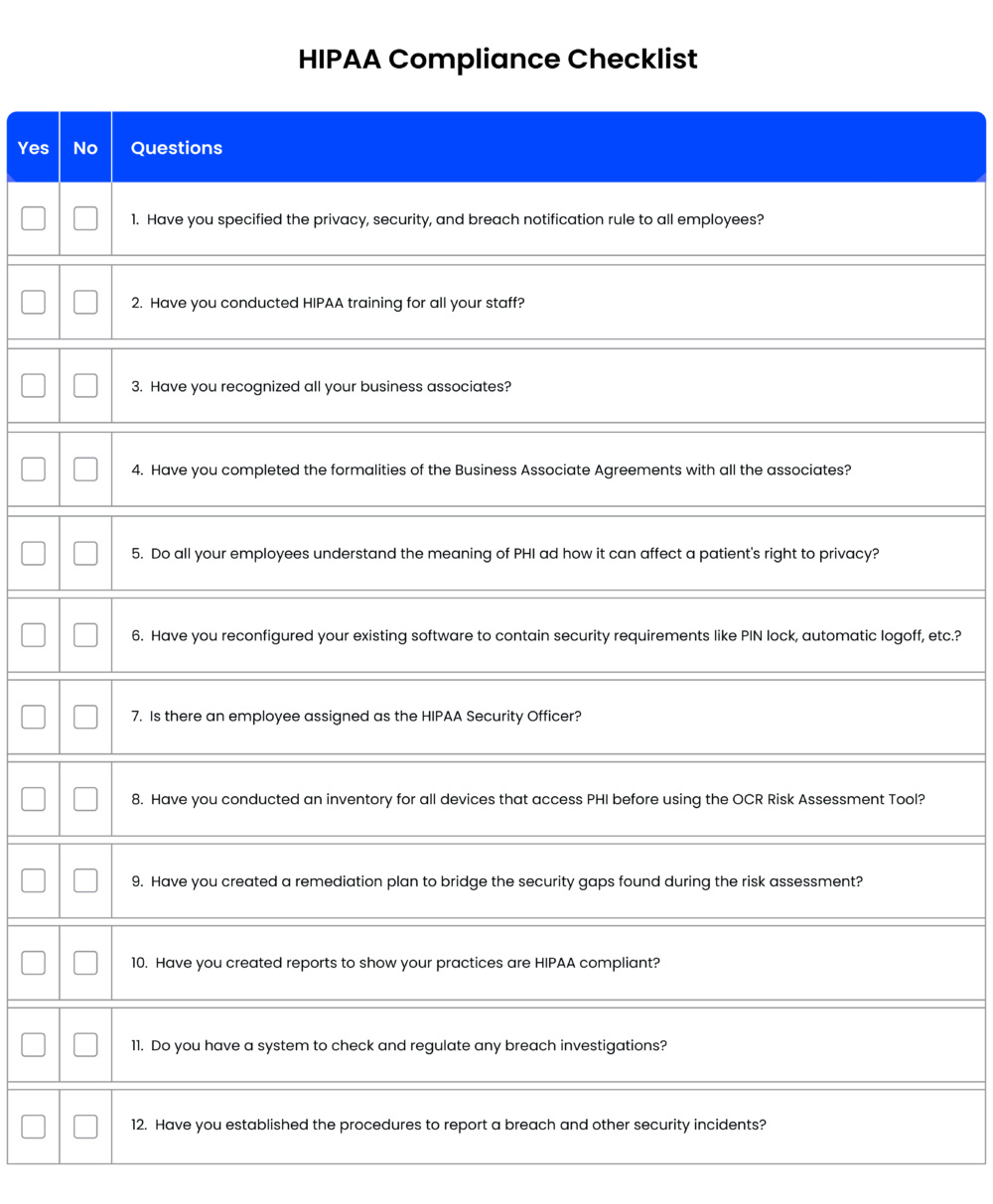
[You can also download the checklist to share it with your team: 12 Rule HIPAA Compliant Checklist]
Looking for a HIPAA-Compliant Healthcare Platform?
If you’re looking for a HIPAA-compliant solution to manage your healthcare practice’s operations and more, a healthcare CRM might be the answer.
An end-to-end patient relationship management platform/healthcare CRM such as LeadSquared, can assist in creating a secure, single-source overview for patient profiles, health histories, appointment schedules, and more.
Additionally, integrating an EHR system within our HIPAA-compliant CRM ensures that providers can manage and access personal health information (PHI) securely. Certified EHR systems allow individuals to request their health information in electronic forms, adhering to privacy regulations.
It can also help facilitate your other significant needs:
- Lead capture and management, allowing you to safely house, search, and share information on potential patients with members of your team.
- Healthcare Marketing automation, enabling compliant outreach through automated communication with existing/prospective patients.
- Engagement scoring, providing the tools to trace engagement behavior and help nurture ongoing customer relationships.
And with a system like LeadSquared, a HIPAA Business Associate Agreement always comes standard.
Get in touch with our team to know more!
FAQs
HIPAA (Health Insurance Portability and Accountability Act) is a set of rules that protects patient health information from breaches and ensures that it stays private and secure. It matters because healthcare data is incredibly sensitive—no one wants their medical history falling into the wrong hands. HIPAA sets the rules for how covered entities, insurers, and even their business associates handle patient data.
Anyone in the healthcare industry handling PHI. This includes doctors, hospitals, insurance companies, and even third-party vendors like billing services or IT providers. If a business interacts with patient data in any way, they likely need to follow HIPAA’s rules. Even healthcare CRMs must have safeguards in place to ensure compliance.
PHI includes any information that can identify a patient and relates to their health. This could be a name, address, Social Security number, medical history, treatment details, or even payment records for healthcare services. If it’s linked to a patient and their health, it’s PHI.
Electronic Protected Health Information (ePHI) refers to any PHI that is created, stored, transmitted, or received electronically. This includes digital medical records, emails containing patient details, e-prescriptions, billing data, and even phone call recordings if they contain identifiable health information. Because ePHI is more vulnerable to cyber threats, HIPAA requires strict safeguards like encryption, access controls, and audit logs to keep it secure.
Penalties can be serious. Fines range from $100 to $50,000 per violation, and in extreme cases, it can also lead to criminal charges. Beyond the legal consequences, a HIPAA breach damages patient trust and can bring a flood of bad press. No one wants to visit a provider with a history of leaking patient data.
Individually Identifiable Health Information (IIHI) is any health data linked to a specific person, like name, birth date, or medical history. PHI is IIHI that is created, stored, or shared by a HIPAA-covered entity (like a doctor or insurer) in connection with healthcare services. PHI is legally protected, while IIHI outside the healthcare system (like in a personal health app) isn’t.
HIPAA classifies healthcare clearinghouses as covered entities, meaning they must follow strict privacy and security rules when handling PHI. Since clearinghouses process medical claims and billing data between providers and insurers, they must encrypt data, control access, and ensure secure transmission.
Yes, but with precautions. Standard email and SMS aren’t secure enough for sharing PHI. Providers must use encrypted email services or patient portals that meet HIPAA standards. If patients want to receive messages via regular email or text, they must give written consent acknowledging the risks.
HIPAA ensures health insurance portability by allowing employees to maintain coverage when switching jobs. It prevents exclusions based on pre-existing conditions and reduces coverage gaps, making healthcare more accessible.
The Privacy Rule governs who can access Protected Health Information (PHI), while the Security Rule sets technical, physical, and administrative safeguards to protect Electronic Protected Health Information (ePHI) from breaches.
The Breach Notification Rule requires covered entities and business associates to report breaches of PHI to affected individuals, the government, and sometimes the media. The severity of reporting depends on the breach’s impact.
A Business Associate Agreement (BAA) is required for third parties handling PHI on behalf of covered entities. It outlines compliance responsibilities, ensuring all parties protect patient data according to HIPAA regulations.
The HIPAA Security Rule mandates technical safeguards, including encryption, access controls, and audit logs, to prevent unauthorized access and ensure EHRs remain secure.
Covered entities can ensure HIPAA compliance by conducting risk analysis, implementing administrative, physical, and technical safeguards, training employees, and following HIPAA Privacy and Security Rules to protect patient data.









